ONE of the north’s biggest construction companies has been targeted by the same ransomware group behind the recent attack on Royal Mail.
The Lagan Specialist Contracting Group (SCG) is the latest victim of the LockBit group.
The company, which is headquartered in Belfast’s Titanic Quarter, confirmed it had “experienced a recent cyber incident”, but said its businesses continue to trade normally.
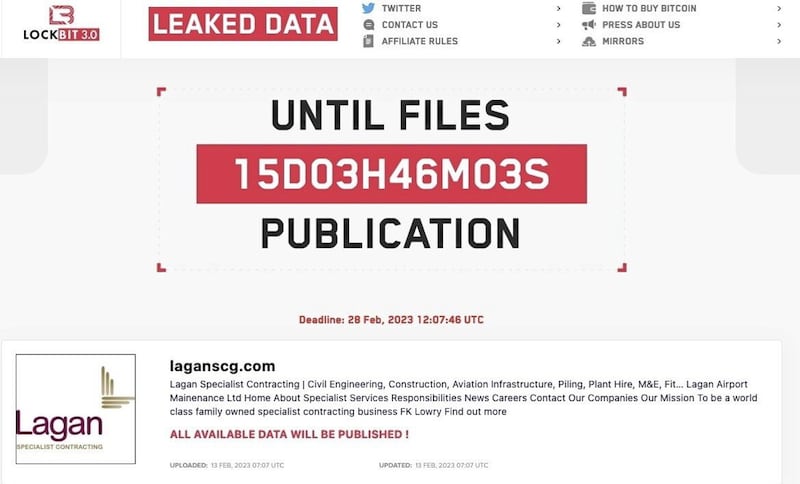
The Irish News can reveal Lagan SCG has been given a deadline of February 28 to pay up or face potentially sensitive being data published online or sold onto third parties.
It’s understood the PSNI’s cyber-crime unit is aware of the ransomware attack.
Lagan SCG’s operation spans a dozen office sites across the island of Ireland, Britain, the USA and Dubai.
The group’s nine companies include H&J Martin, FK Lowry, Charles Brand and Rosemount Homes.
But the Belfast firm is also increasingly active in the aviation sector, building complex airport projects and runways, with customers ranging from London City Airport to the RAF.
The Lagan SCG attack was announced on the dark web on February 13, via a public website that publishes details of LockBit attacks.
LockBit is the name given to both the malicious software (malware) used to target businesses and the organisation behind it.
But cyber security insiders said the LockBit group also works as a ransomware-as-a-service operation, with a core team that sells its malware onto third parties to carry out attacks.
Ransomware attacks usually originate from ‘phishing’, where users are tricked into downloading a piece of malware.
Once hackers are inside, companies typically face a two pronged attack, also known as “double extortion”.
On one hand they will have their files and IT system encrypted, with the key to unlock only provided on payment. Companies also face threats of having sensitive data being leaked online or sold to the highest bidder.
A spokesperson for Lagan SCG said: “We have concluded our investigation, engaged with the relevant authorities and kept employees and clients aware of matters.
“Our businesses continue to trade as normal. Events of this nature are unfortunately increasingly common.
“We will continue to implement robust security controls to further ensure the safety of our systems.”
The dark web site that announced the Lagan SCG attack, known in the cyber security world as the ‘LockBit leak site’, last week published a transcript of the negotiations with Royal Mail, which appear to have ended without payment.
The chat log detailed how the LockBit group demanded 0.5 per cent of Royal Mail’s annual turnover, equivalent to around $80 million (£66.5m).
The log suggests that over the course of four weeks of exchanges, Royal Mail’s negotiators were at one point prepared to offer $4m.
It has been reported that companies usually face demands to pay the ransom in cryptocurrency.
Turnover across the Lagan SCG’s various companies was in excess of £100m in 2022.
It’s thought the ransom being demanded from the Belfast business is in the six figures.
A cyber security expert familiar with the attack on Lagan SCG said it’s now generally accepted within the industry that around 80 per cent of UK firms targeted end up paying some form of ransom, a rate higher than in other parts of the world.
Those who pay are removed from the dark web leak site.
Earlier this month it was reported that the Dublin-based financial software group Ion Trading, which has offices in Belfast, paid a ransom to LockBit.
The amount allegedly paid was not specified, but Reuters reported that a decryption key had been delivered to allow Ion Trading to unlock the infected machines.
An Irish repair management firm and a number of UK businesses, including a logistics firm and a fuel company, are among the companies who have had their data published after apparently refusing to meet the ransom demands.
While the PSNI is aware of the Lagan SCG attack, the availability of resources available means the response to the surge in ransomware attacks is increasingly falling to cyber security experts in the private sector.
Insurance companies are also understood to be at the forefront of advising companies on how to respond, with cyber-security consultants and negotiators typically brought in.
The PSNI was contacted for comment, none was available at the time of going to print.




