ACCESSIBILITY to data, finances, and people has never been easier thanks to developments in mobile technology. We can pay for almost anything, call anyone in the world at any time and even open our hotel room doors, with our phones.
Smart chip technology has revolutionised how we live our lives, but we don’t often realise just how much information is floating in the ether following every transaction or interaction.
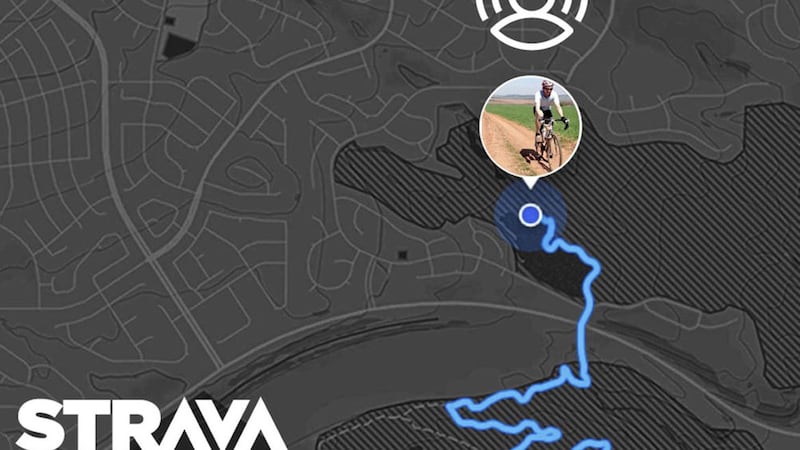
Strava, the activity tracking software favoured by runners, cyclists and swimmers the world over for following their exercise routes, was recently in the news following it publishing every single movement and routine registered by its users.
The reason it made the news was due to users in the military flagging their routes at army, naval or air bases around the world, including highly sensitive and top-secret locations.
This of course had the chance of being catastrophic and potentially life threatening to those who live and work at these bases, highlighting how easy this information was to access and understand.
While not necessarily safeguarding nuclear codes, companies and organisations the world over contain information, contact details and personal data relating to staff, suppliers and clients, sometimes thousands of names, numbers and addresses.
In May of this year, the new General Data Protection Regulation (GDPR) will come into force, meaning that the use of this personal data is going to be much more strictly policed, with hefty fines as a result of any breaches.
The GDPR “applies to any information relating to an identifiable person…and the way organisations collect information about people” (ICO). So, whether this involves a spreadsheet or manually written hard copies in a filing cabinet, how this data is stored and used will now be under more scrutiny than ever before, causing many sectors notable concern.
With much of this data on shared servers, it is a company’s duty to ensure it is protected from unauthorised or unlawful processing and used solely for the purposes it was intended for upon receiving or securing.
In essence, any member of staff who is involved with the processing and storage of data must be familiar with both the official data protection training guidelines and their own organisation’s data protection policy, via a designated Data Protection Officer (DPO).
Taking into consideration the number of businesses that have to update spreadsheets on a frequent basis, whether contact telephone numbers, addresses or changing a maiden to married surname, much of this activity is undertaken by interns, office juniors or secretaries, placing an increased level of “responsibility” on the wider team as a result.
Even the simplest client Christmas card list will fall under the watchful eye of GDPR so businesses need to be cognisant of how easily accessible these files can be. The security of internal networks is essential to ensure information does not leak out and in achieving good standards of corporate governance, reducing and managing risk, and aiding in regulatory compliance efforts.
With more employees being ‘mobile’ for business purposes, the importance of incorporating endpoint security, relating to any device that connects to a shared network, is increasingly becoming reality.
By integrating network and endpoint security, organisations are afforded greater visibility over the entire range of security threats that they face, with the hope this will flag and overcome any shortcomings or potential breaches in the light of GDPR and allow for as smooth an introduction to the new legislation as possible.
:: Eric Carson is director of Rainbow Communications and can be contacted via www.rainbowcomms. com. Rainbow Communications can also be followed on Twitter - @ Rainbow_Comms.